RG-WALL 1600-Z5100-S
New-Generation Z Series Enterprise-Level Firewalls
Flexible expansion, simplified deployment, and cloud O&M, fully unleashing security defense capability


Flexible Firewall Performance Scalability, Satisfying Service Upgrade and Development Demands
By adding software licenses, you can increase network throughput of RG-WALL 1600-Z5100-S by 3-10 Gbps. Each software license increases the throughput by 1 Gbps.
In addition, the high-performance free SSL VPN is provided, allowing up to 1000 users at no extra cost.

Five-in-One Firewall License for
Comprehensive Network Security Defense
The five-in-one license for intrusion prevention (IPS), antivirus (AV), threat intelligence, URL filtering, and application identification enhances the network defense capabilities of your organization in an all-round way, dramatically improving the security of data and systems.


-
Unmatched Protection: Ruijie's IPS signature library covers over 15,000 entries for detecting various cyber threats.
-
Stay Ahead of Attacks: With more than 90 classifications, including mining and ransomware, our IPS is at the forefront of security technology.
-
Continuous Improvement: Weekly updates and a leading number of monthly additions ensure that your network security is always one step ahead.

-
Millions of Signatures: Ruijie TIANMU Security Lab cooperates with a leading antivirus company and has developed over 10 million AV signatures for the Z series firewalls.
-
Accurate Detection: With an accuracy rate of 99.97% and a zero false positive rate, Ruijie's AV technology is widely recognized for its high precision.

-
TI is an important concept in cyber security and involves the collection, analysis, and dissemination of information on potential security threats from various sources. Ruijie Z series firewalls leverage a local TI signature library and employ TI for threat hunting to identify undetected threats or attackers on a network.

-
Comprehensive Traffic Management: Our NGFW's application control signature library can recognize 7200+ applications. With Deep Packet Inspection (DPI), the NGFW can accurately identify and control P2P traffic.
-
Granular Access Control: The NGFW categorizes and manages application traffic with high precision, allowing for tailored access control policies that align with your business needs.
-
Proactive Threat Prevention: The NGFW automatically detects and blocks malicious applications and attack payloads, safeguarding your network against emerging threats.

-
URL Identification: Ruijie firewall's URL signature library can precisely categorize web traffic in real time.
-
Secure Web Access: You can configure custom security policies to permit or deny web resource access.
-
Threat Interception: The NGFW detects and blocks malicious websites to prevent phishing and malware.
Cloud, Make Your Business Easy
Self-Organizing Network
Remote Policy Configuration
Remote Firmware Upgrade
License Activation on Mobile App
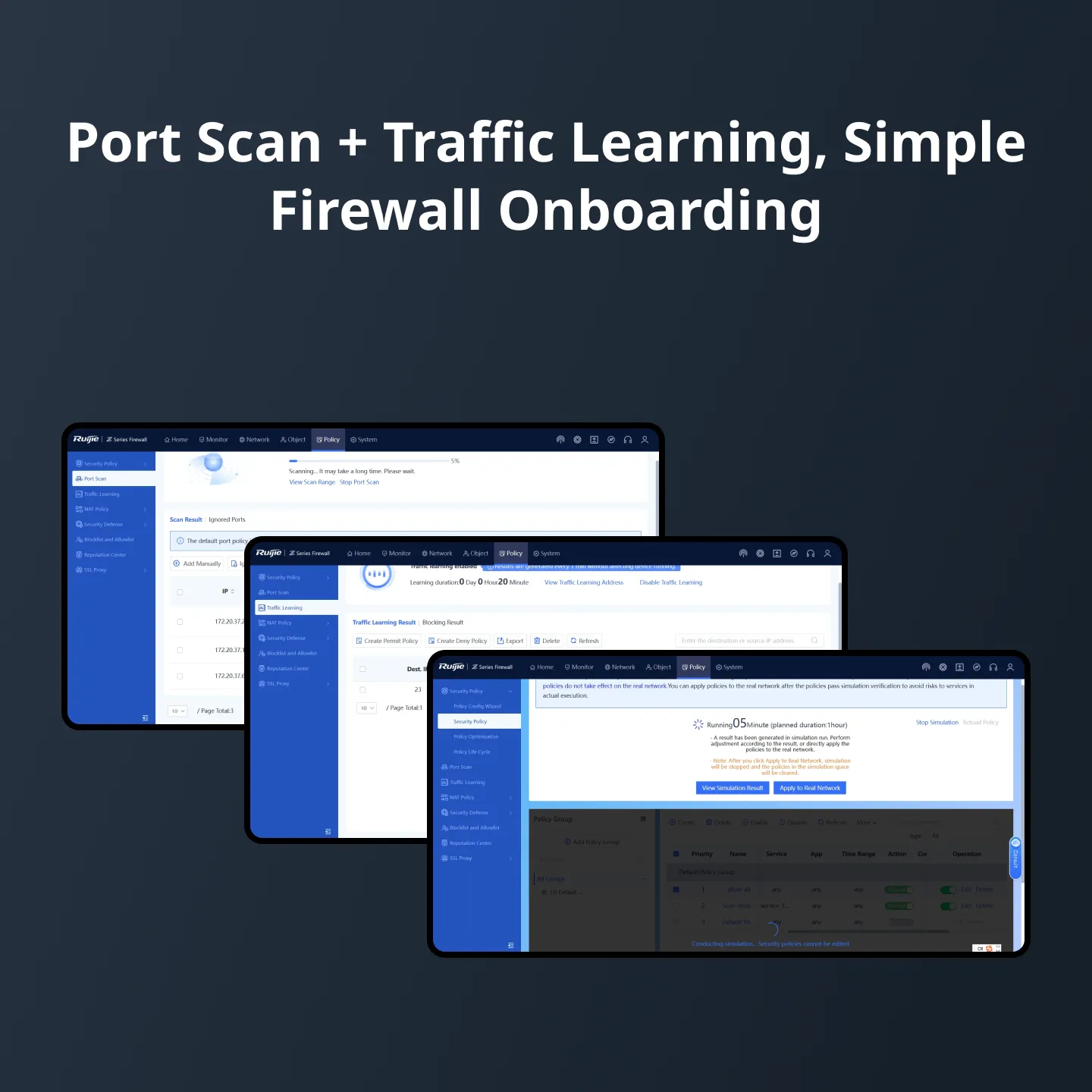
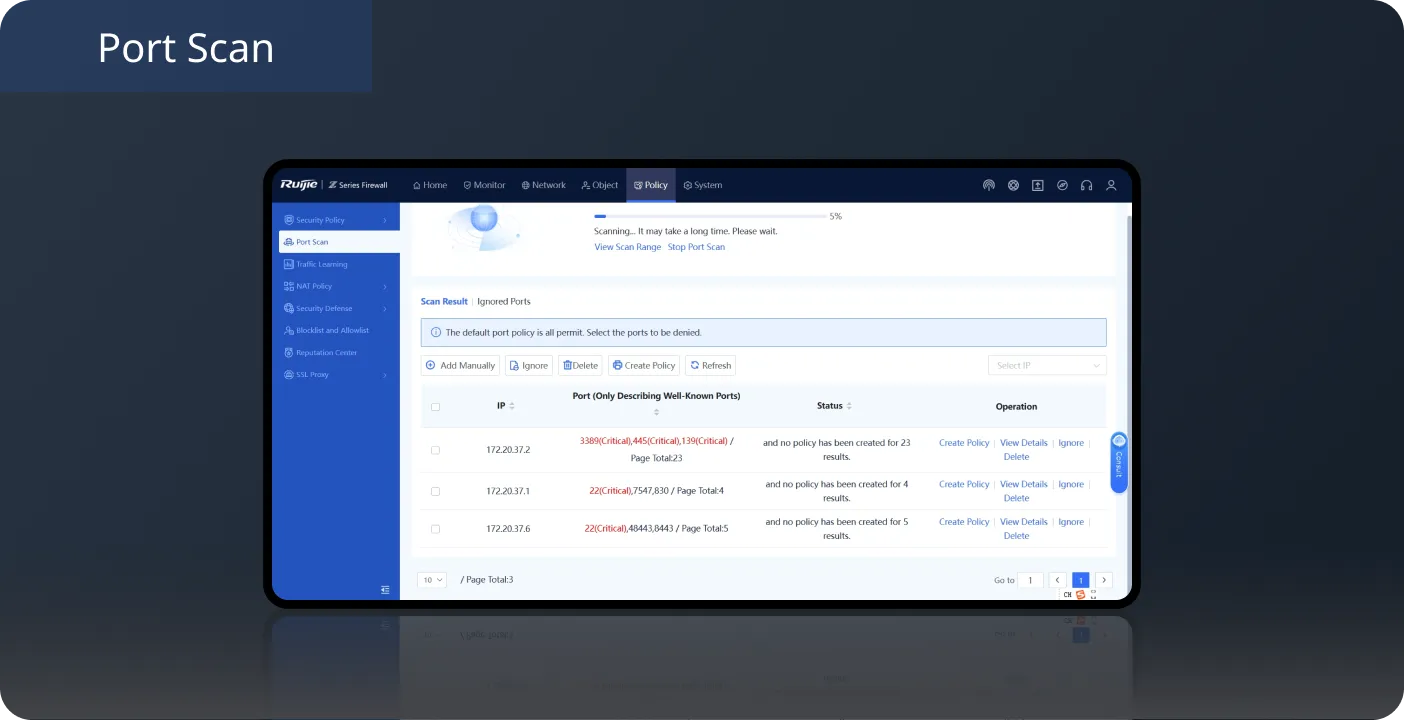
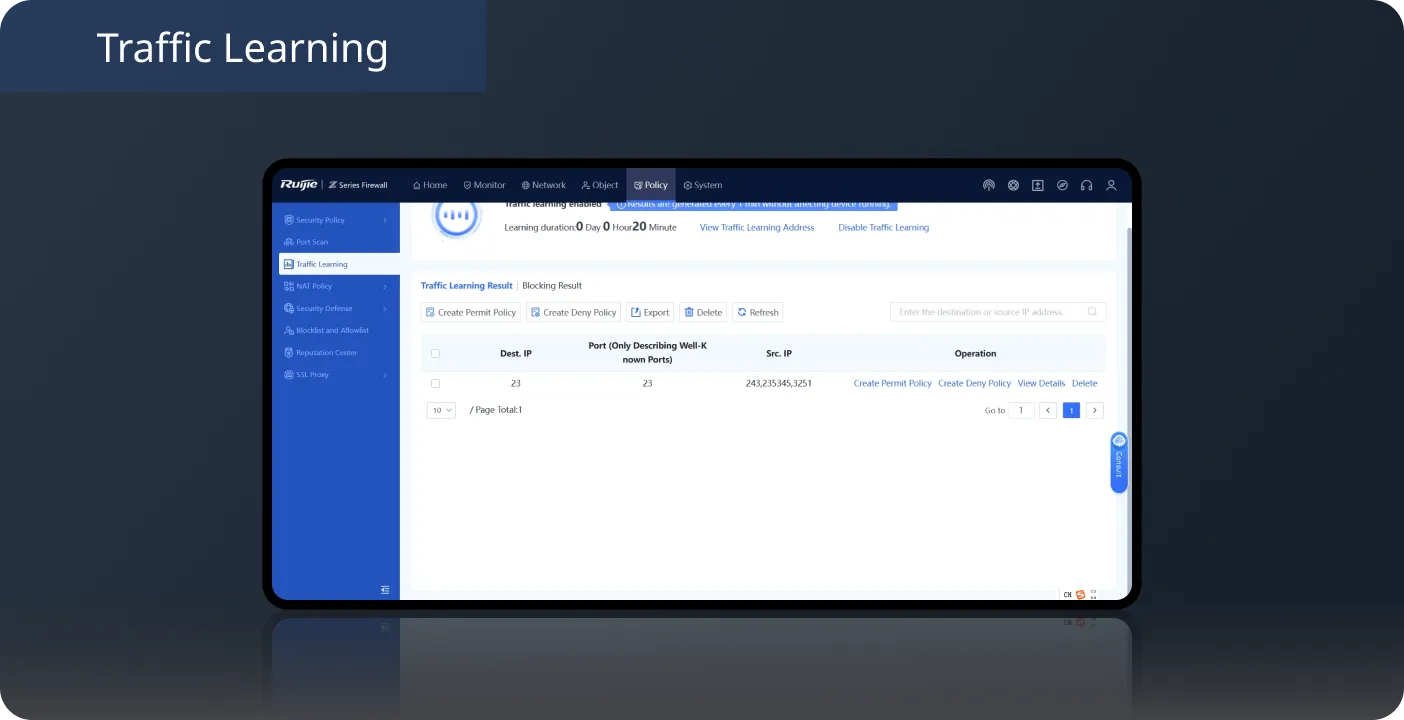
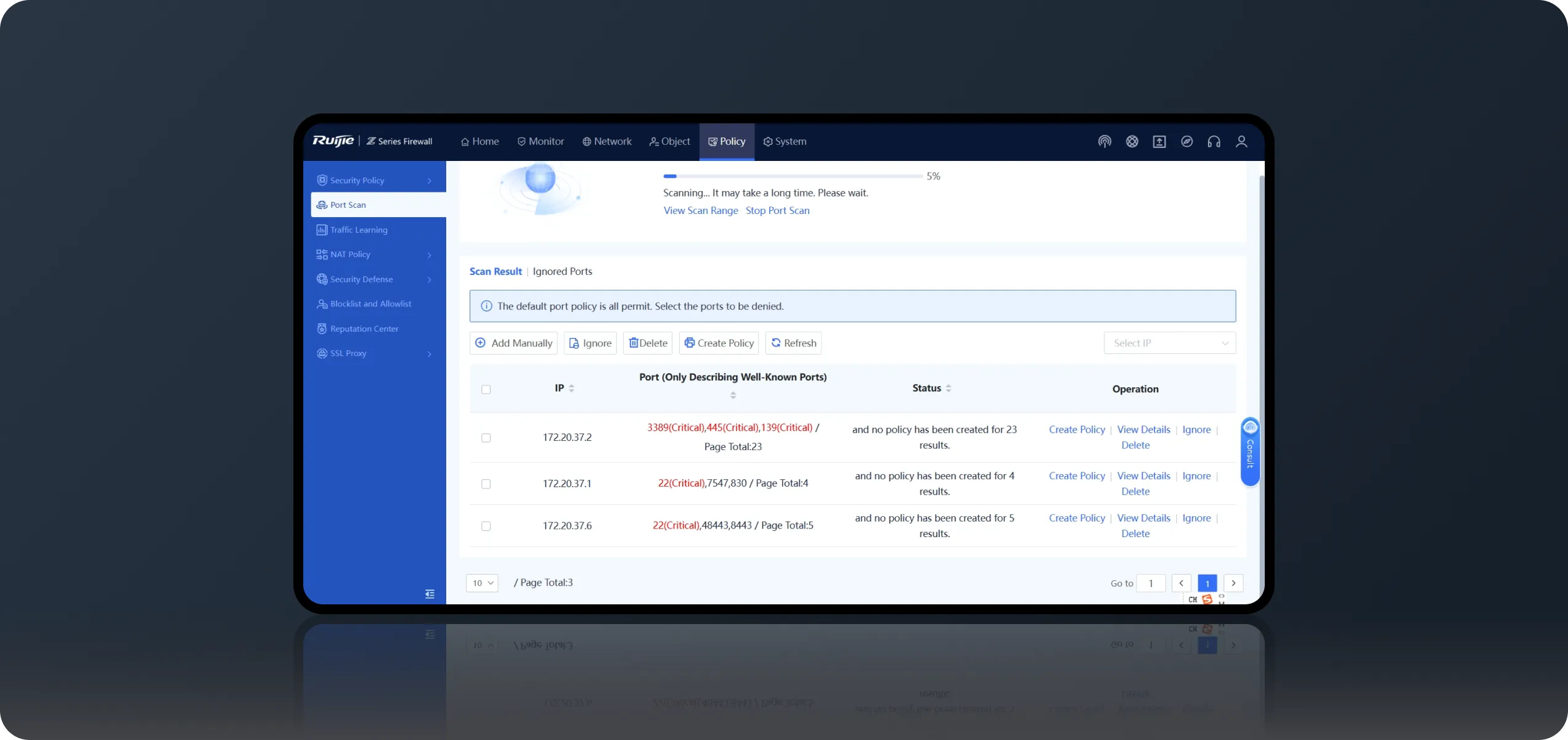
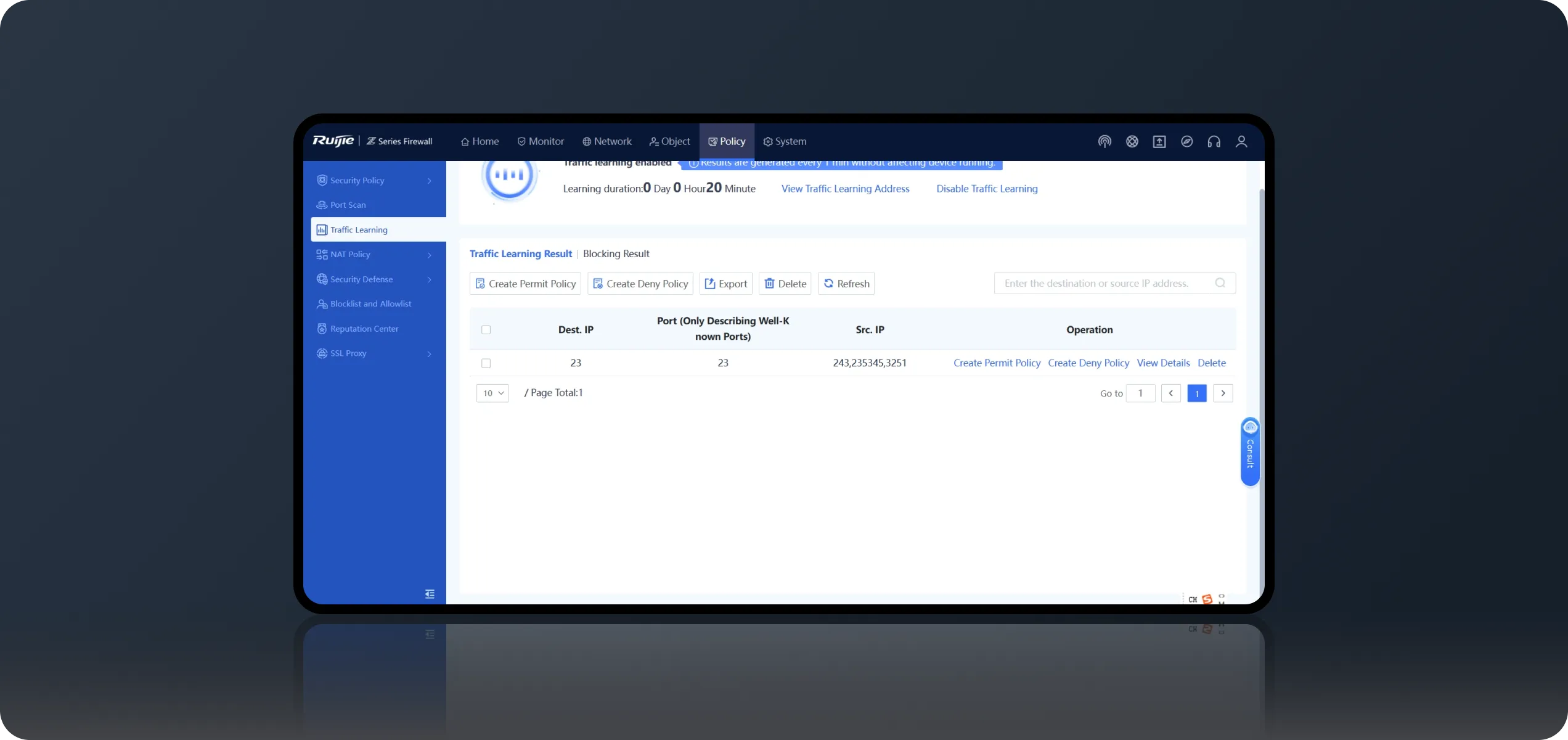
Port Scan + Traffic Learning, Simple Firewall Onboarding
During deployment, use Port Scan to automatically identify the IP address and port number of a service system, and then enable Traffic Learning to automatically detect the service access relationship on the live network. You can also generate access control policies based on ports with one click, and complete firewall onboarding without professional knowledge.
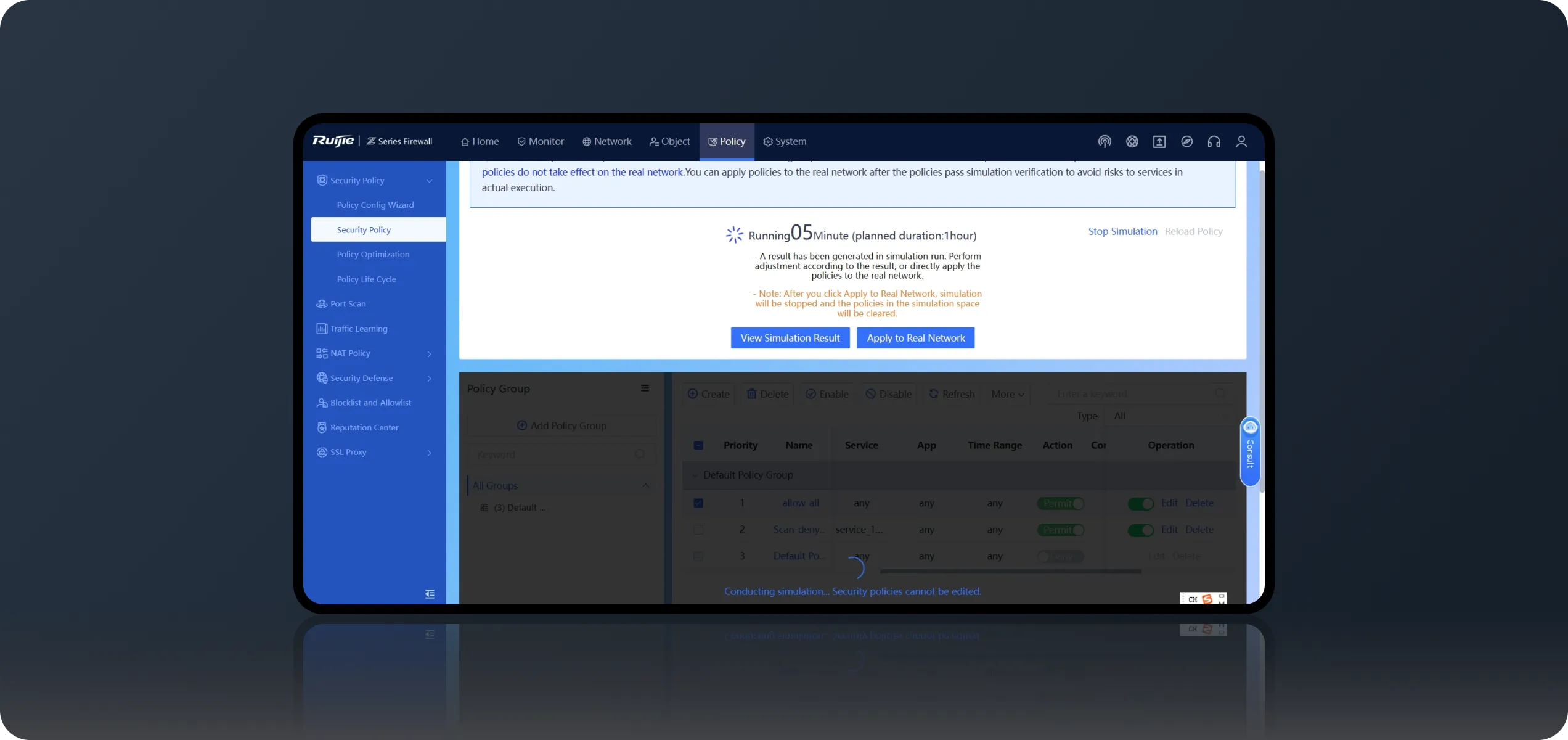
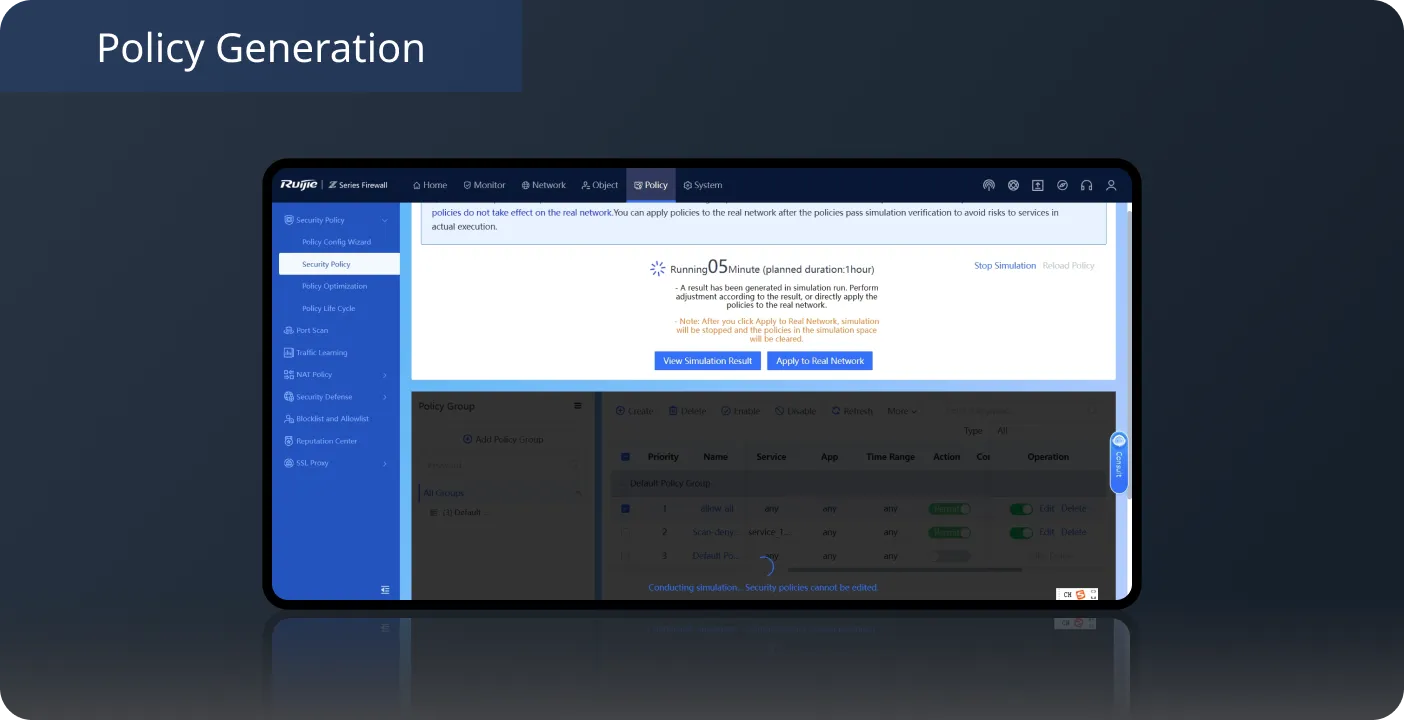
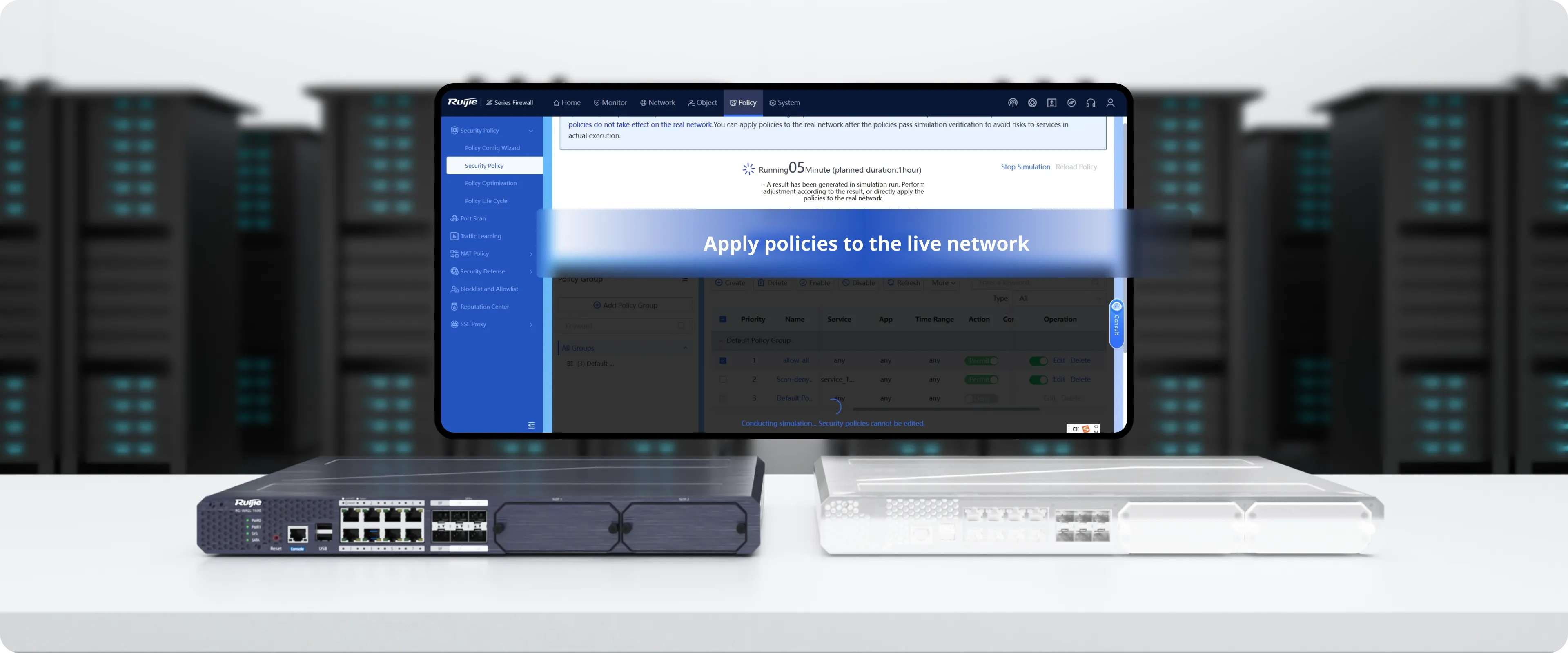
Policy Execution After Simulation,
Policy Optimization Anytime
Verify policies using real traffic in Policy Simulation Space without affecting actual services or compromising network performance.
Apply policies to the live network with one click after verification.
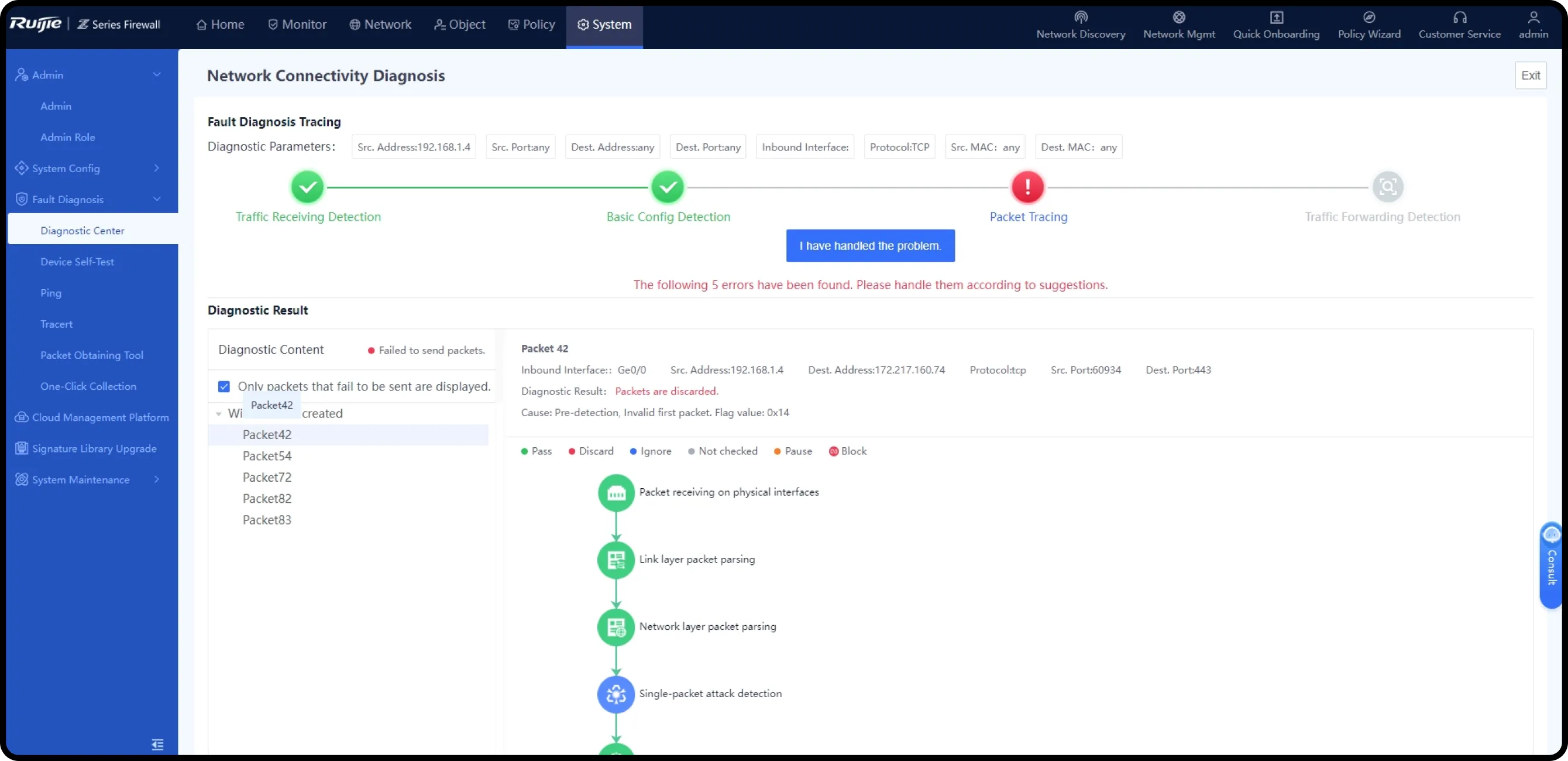
One-Click Fault Locating
in the Intelligent Diagnostic Center
The intelligent diagnostic center supports automated analysis of network faults and provides a one-stop troubleshooting wizard for O&M personnel to quickly locate and resolve faults.